Kaseya spring release: EDR
This page details each EDR release launched during the Kaseya Spring release.
Rollback System Service update
Rollback System Service build 1.3.4.146 coming Thursday April 10
In previous Ransomware Rollback versions, some users experienced crashes when working with files that were in use by other applications, such as Ebv2. This could disrupt file operations and, in some cases, result in file corruption. With Build 1.3.4.146, we've fixed the issue by improving how the Rollback System Service handles these situations. Going forward, Ransomware Rollback should no longer crash when encountering locked files, resulting in a more stable and reliable experience.
New feature
Dark Mode
We're excited to introduce the Dark Mode display option. This alternate aesthetic can be selected from the Account menu.
Enhancements
Redesigned Alerts table
The Alerts table has been redesigned to provide a more engaging and personal experience and includes the following enhancements:
- Filter columns: Filtering options are now available next to the column headings. The filtering options you select are listed in the field above the table. If two or more filtering options are selected for the same column, the number of selected options is displayed.
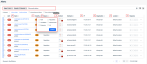
Column filtering replaces the single Filter menu that was provided above the table.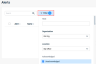
- Resize columns: You can resize column width by dragging a column header's boundary line.
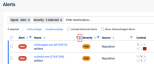
- Select columns: With the Column Options icon, now you can select the columns to display in the Alerts table.
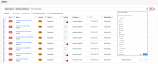
The following options are available above the table: Acknowledge, Unacknowledge, Include Historical Alerts, and Show Acknowledged Alerts.
For more information about the Alerts table, see the article Working with the Alerts page.
Uninstall jobs now remain active for six months
Previously, when uninstalling a device from the EDR platform, the uninstall process remained active for seven days. Therefore, when an offline device was uninstalled, the device would only be uninstalled if it was back online (checked in with platform) within seven days of the start of the uninstall process.
Now, the uninstall process remains active for six months. Meaning, an offline device will be uninstalled if it is back online within six months of the start of the uninstall process. If the device checks in after the six month time frame, it will reappear on the Devices page and need to go through the uninstall process again.
See the article Uninstalling the Datto Endpoint Security agent.
Enable devices from the Devices table on the Locations page
If an endpoint's agent repeatedly fails to download an update from the EDR platform, EDR will disable the endpoint. You can attempt to enable the device from the Devices page, but you now have the option to do so from the Devices table on the Locations page as well. After enabling the device, it will attempt to complete the update. 
For more information, see the article Working with the Location details page.
Requirements warning for endpoints
To improve device management practices, the Devices table will display a warning icon for devices that do not meet the minimum agent requirements stated in the article Hardware and operating system requirements
Easy access to device details in RMM
To ensure quick and easy access to device details in your RMM, the Open device in RMM button now remains active even when a device is offline.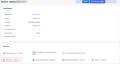
Bug fixes
- Some AV alerts were incorrectly labeled with the Quarantine response indicator even though the AV policy used an Alert Only configuration. This issue has been resolved.
- Certain Instant notification profiles reset their configuration due to rate limits. We have improved the handling of this condition to avoid the configuration resetting.
Enhancements
System notification added for invalid suppression rule
We have created a new system notification that applies when a suppression rule is no longer valid. The notification will display when a location or organization for which a suppression rule is assigned has been deleted. This will help you manage your suppression rules and make updates as needed.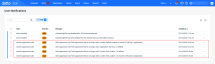
Improved agent download process
We have updated the process for downloading the agent to help users identify the correct agent for their endpoints. Clicking the Download Agent button on the Location page displays a revised Download Agent modal. The agents are listed in the Processor drop-down list and includes a new Mac naming scheme, MacOS (Intel) and MacOS (Silicon).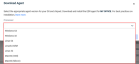
Copy Command Line has been enhanced to remove some of the manual steps originally required when performing the installation steps.
NOTE The Copy Download Link button has been removed.
Updated Datto Antivirus policy page
The Datto Antivirus policy page has been updated to reduce the number of clicks required to set options and to make it is easier to pivot across AV and DNS settings. The new Policy Rules section includes the Antivirus tab and the DNS Secure tab.
On the Antivirus tab, you can easily set the policy's operating mode in the Security Profile section. The new Disabled option allows you to turn off both the Real-time Protection Scan and the Scheduled Scan functionality. You should only use this option for diagnosis and testing.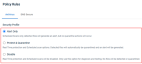
The Exclusions section has been compressed and includes the Universal AV exclusion option and the new Add Exclusion button.
Instead of entering folder, file, and process exclusions in their respective sections, now you enter the exclusion path and select the exclusion type in the Add Exclusion modal.
The DNS Secure tab provides the same options as before. However, now you select Threat Categories via check boxes instead of enabling toggles. In addition, blocked domains and trusted domains are added in the Domain List section, instead of in their own sections.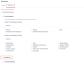
See the articles:
Edit Policy confirmation dialog box
If you navigate away from an Edit Policy page and have unsaved changes, a new confirmation dialog box will be displayed. Click OK to navigate to the desired page without saving your policy edits or click Cancel. Then, on the Edit Policy page, click Save.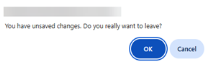
New article: EDR rule updates
The new EDR rule updates article identifies application code changes made to EDR rules. If you notice you are receiving new alerts or there is a drastic change in volume for a certain type of alert you receive, you may be able to identify the reason in this article.
Each table includes the name of the rule, the type of change (new rule, edited rule, or deleted rule), rule details, and the impact the change may have on the customer. The date identifies when the change was live in the application.
Artifacts
agent.linux-amd64.054e2ed60270d11b77f41212a22316de545f1d010e7ab9f53188877c0dfdd752.bin.gz agent.linux-arm64.5fdda878aae40e95d2878fb3aed17e886b5396c883a788fb9f4a6c1c67087229.bin.gz agent.linux-x86.d2679cba78f6ed99d2ee4c2252c1c33f3c5c8ce6aaa53a42472a00e965014f00.bin.gz agent.macos-amd64.dc76a68a4cb75cd5991efc878af140228242602d69642fa235f76190cda16dfc.bin.gz agent.macos-arm64.9b262b246c48cbb0dad5cf5536d2c904a4e3db7f057c429e13d205a4e7105b98.bin.gz agent.windows-amd64.8b726e95b543d1b790020b700f1c5af845abe0384dd89ff1c087b39be8dadfcf.exe.gz agent.windows-x86.bccc4016d9e5bd75f6ddb0c7849fe4e166139826b8848bee43925760b25372b6.exe.gz integrator.windows64.62490e37fa10357387e4c8431386b0a0543f2d164d5c52e64eb68c6a807774a3.exe.gz
Enhancements
Endpoint scanning capabilities optimized
We have optimized our endpoint scanning capabilities by decommissioning memscan uploads, which were highly resource-intensive. This change enhances overall system performance without compromising security, as our advanced detection mechanisms continue to provide robust protection against threats.
Bug fixes
Users may not have been able to disable system notifications if previously enabled. This can include System notifications on inactive, isolated, and disabled devices. This bug has been identified and resolved.
New Features
Automatically delete aging devices
To help manage license usage and the Devices table, you can enable the new Automated Device Delete feature. The feature will automatically delete devices that have not been active within the last 30-365 days. It is located on the Admin > Settings > General page. You configure the specific number of days for which a device must be inactive before it its deleted.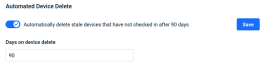
Before enabling this feature, we recommend verifying your Devices table is clean and up to date. Then, enable the feature and specify a time frame that is safe for your business. For example, may be start with devices that have not been active for 90 days then adjust the number of days as needed.
For more information, see the article Navigating the Admin page.
Automatic Device Group
To make onboarding new devices and managing device group policies more efficient, we have implemented the new Automatic Device Group feature.
Now, when you add a new device, you can automatically assign it to a device group based on the device's operating system (Linux, MacOS, Windows Workstation, Windows Server). The Automatic Device Group feature is available when creating or editing a device group on the Organizations > Devices > Device Group page.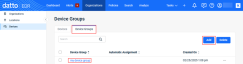
Enable the feature selecting the desired operating system for the device group.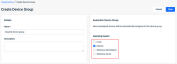
IMPORTANT The Automatic Device Groups feature applies when adding new devices only. Devices that existed before you enable the Automatic Device Groups feature will not be auto-assigned to the OS-based device group.
To learn more about the new Automatic Device Groups feature, see the article Creating device groups.
Enhancements
Pagination added to additional pages
To eliminate extensive scrolling, pagination functionality has been implemented on the following pages:
- Respond > Responses
- Respond > Queued Responses
- Admin > Activity > General
- Admin > Extensions > Extensions
- Admin > Extensions > Global Variables
Example
Bug fixes
We resolved an issue where VSA integrated EDR tenants appeared to have their integration disconnected temporarily in the UI. Improvements have been made with this release to ensure the integration remains connected.
Enhancements
Verifying format of Datto AV exclusions
We discovered users are creating some Datto AV exclusions that will not work as expected due to improper formatting. Additional formatting checks have been implemented to help users properly create Datto AV exclusions. Therefore, formatting will be validated as you create an exclusion. If the formatting does not meet the requirements, a warning banner will be displayed, as shown in this example.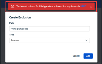
To learn about the Datto AV exclusion formatting requirements, see the article Working with exclusions in your Datto AV policy.
Updated device download and install commands
We have updated our device download and install commands. Previously, the commands did not include the ability to automatically download the agent. Users had to perform steps to download the agent to an endpoint and then run the install commands. Now you can go to your location, click the Download Agent button, then click the Copy Command Line button.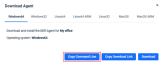
This will provide a full command that will download and install the agent with the correct location identifiers.
Users can delay reboot reminder when first installing Datto AV
Historically users may have seen repeated reminders to reboot the endpoint to complete Datto AV installation. This could be disruptive to users who could not restart workstations at that moment. Now, an end user can acknowledge the banner to reboot and that banner will not reappear for three days. This will allow users to reboot at a more convenient time.
Artifacts
agent.linux-amd64.cf5f1b6df4fcea7ca67a0a7dfe419c80da1d351b6f6cb68b82e68f9711aa06e9.bin.gz agent.linux-arm64.2f9932dcf513a153eb575ab28650066cf88e88b70832a47cbab52f6ab54b9bc7.bin.gz agent.linux-x86.6ece6ed005ed81686f718420b8d3682cc3322074b173ee8643ef5856b426561f.bin.gz agent.macos-amd64.21b385fce98e926cf84dde8f5b2a49c219328026a69cd657bbddd89375af91b5.bin.gz agent.macos-arm64.523a07e9bcc0ffbf4ce64609a4e9aa6077065e4be5b4ba68bee0b6534a233c64.bin.gz agent.windows-amd64.5edcacb31aefdc0c05afb58f2efca3a3f67ac75b1bbe5786bc30f5b9c8b68df8.exe.gz agent.windows-x86.8afaa04773755577086a1f70d721878edb6ce2b3bd42f0c936310d51c71d58f7.exe.gz integrator.windows64.62490e37fa10357387e4c8431386b0a0543f2d164d5c52e64eb68c6a807774a3.exe.gz
New Features
View historical alerts
When applying a filter on the Alerts page, results from the last 30 days are displayed. We are excited to announce users are now able to view alerts older than 30 days directly in the EDR portal.
To view historical alerts, on the Alerts page, click Filter. Select your filter options then scroll to the bottom and select the Include Historical Alerts check box. Click Apply.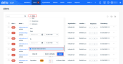
All alerts matching the filter criteria, regardless of when they were created, will be listed in the Alerts table.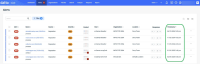
Enhancements
Integrated customer billing - additional metrics
We have made improvements to our Integrated customer billing integration. We are now sending additional metrics that you can learn more about in the article, Integrated billing via Autotask and Kaseya BMS
Artifacts
agent.macos-amd64.db3f40a939b72ff145a26801b96ed29df7df3003b091972d70263f1d0c20d757.bin.gz agent.macos-arm64.e3d385da3cac64384355dbc49e9d09035dc101b36c268caf74e376b67c778ede.bin.gz agent.linux-amd64.1d65baea07e84e925c5138d06e775019bfe344b03ebbbbc582c874138098ae1d.bin.gz agent.linux-arm64.e3d86b30543aa54f417b97e8299de54e28a5a121fd953511e68706c75b3589c7.bin.gz agent.linux-x86.90b4a3ec3a633abf8ae2ea0ab532397170836ecc2a265e3f44eac4ae674bd61e.bin.gz agent.windows-amd64.ba39b0e46aea9d719886f724473c2a586ed7b736b1c89195e61501fb4d0191de.exe.gz agent.windows-x86.1754a067df68d17814eec16e548226c9ee2ef6f2039a4e09457bf082163c46bb.exe.gz integrator.windows64.26ddd43e8fac5bd0308ea6d17b967e44b84aa393937170d8bbfd7d121585a757.exe.gz
Emergency Update - DNS Secure
Due to many sites being categorized as “unknown,” users were experiencing issues with accessing websites. To avoid future disruptions we are releasing an update that will remove the Unknown option from the DNS secure policy. All other categories have been thoroughly tested and show no signs of mis-categorization.
Enhancements
Unmap Autotask, EDR integration accounts
We are excited to announce users are now able to unmap accounts in the Autotask/EDR integration. 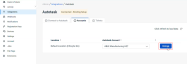
Scan button more accessible
We have improved the ease that EDR operators may launch a scan against devices in their estate. The Scan button is now available on the Organizations, Locations, and Devices pages so users can easily initiate a scan.
Scan button on the Locations page
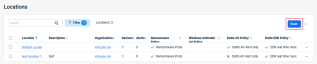
Policy descriptions are now optional
When creating a new policy, entering a Description is now optional.
Notifications now include isolation events
System notifications in the platform now include isolation events initiated by your Ransomware Policy.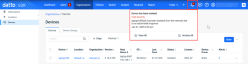
Enable notifications for disabled EDR agents
Users can now configure system notifications to be raised for Disabled EDR agent events, enhancing your overall visibility into the estate health.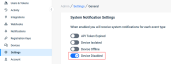
Bug fixes
- The Synapse Score field was included in our Daily notifications email. We have improved the Daily notifications email to have a similar look and feel to other UI elements.
- The Executive Threat Report did not increment for certain Mitre Rule Tactics for some users. This issue has been resolved.
- Resolved an issue where some users could not reconnect their Autotask PSA integration in the EDR portal after they had disconnected the integration.
- The alert count on the Devices table and Device Details page did not match the number of alerts listed on the Alerts page for the same device. This issue has been addressed.
- Dashboard widgets were counting suppressed items. The Dashboard logic has been updated and the widgets now only count alerts that have not been suppressed.
- The enter key on the Number Pad portion of certain keyboards was not accepted by the search bar in the UI. This issue has been resolved.
- The issue has been resolved where users with the Analyst role were not able to create device groups.
- Pagination preferences users set on the Alerts table were resetting when responding to an alert. This has been resolved.
- Column sorting issues in the Organizations table have been resolved.
- When creating Microsoft Defender policies, the issue has been resolved where the spacebar failed to create a space.
Artifacts
agent.linux-amd64.bcaf4f5aa30a3466e743c3d21b070d7ae91ae1dfa54516b60d50a6bf45918af1.bin.gz agent.linux-arm64.11dbbe62e44cdd9510f3b3877743167e94c3849258fc94ec1bba0367bb84a3ff.bin.gz agent.linux-x86.8562a87727207ce2345adfa849ee3f91c02d82d74b004e2b2cec2d166e01352d.bin.gz agent.macos-amd64.73dadf3a442e610765e579e643092dc917901f143746823028ee548501611257.bin.gz agent.macos-arm64.0fd724d35cabb0da0bebb7bc4d580b752f6e68543a40438b30ce672d7faa1bfd.bin.gz agent.windows-amd64.bf92819742768f556b81b41c1e6706b3dab8c65d1b2344b91534f4911aa7805b.exe.gz agent.windows-x86.edd3f6facfc64ec534bfb38d72f491a2c0fe8c7c20fd2addcbfc7634b6b4d65d.exe.gz integrator.windows64.62490e37fa10357387e4c8431386b0a0543f2d164d5c52e64eb68c6a807774a3.exe.gz
New Features
Datto AV for macOS
Protect your macOS endpoints with Datto AV! Deployment and management are as seamless as they are with Windows. Simply configure and assign a Datto AV policy, and it will automatically deploy to any macOS endpoints within the assigned locations. Learn more in the article Datto AV for Mac
DNS Secure
Introducing DNS Secure, a new security layer built into your Datto AV policy to block user access to malicious websites. Safeguard users from phishing, spam, malware, and other harmful web domains. See the article Configuring Datto DNS Secure.
Real-time Protection Monitoring options
Users can now manage more of their EDR agent settings in their EDR policies. These settings, such as Memory scanning, can help balance security and resource availability.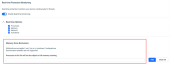
For more information, see the Datto EDR policy section in the article Working with the Policies page.
Tamper Protection in EDR Security Policies
Tamper Protection is now integrated into EDR policy configurations. It restricts service options and ensures the EDR service remains operational.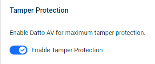
Learn more about tamper protection in the article Understanding EDR and AV tamper protection and refer to the Datto EDR policy section in the article Working with the Policies page.
Submit Datto AV false positive files
Datto AV users now can submit known safe files as false positives by selecting Policies > Datto AV File Submission.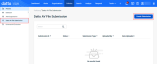
Here you can create a new submission. 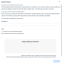
This is a great feature to use for proprietary software. Just submit your files prior to release and those new hashes will be marked as safe.
See the article Datto AV File Submission
EDR alerts in VSAX
For VSAX integrations, EDR alerts can now be received in VSAX. Go to your VSAX integration in the EDR portal and on the Settings tab, enable the desired alerts.
For more information, see the Send EDR alerts to VSA 10 section in the article Configuring the VSA 10 integration.
Enhancements
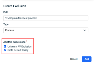
Create a Universal AV Exclusion within a Datto AV alert
When creating an AV exclusion via the Create Exclusion button within a Datto AV alert, you can now add the exclusion directly to the Universal AV Exclusion table. You still having the option to add the exclusion to your current Datto AV policy as well.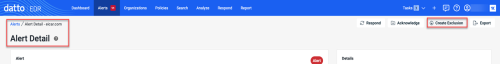
EDR uninstall log
In the event the EDR agent is uninstalled locally, we now create a final log and send it to your EDR portal. This way you can audit uninstalled agents and identify the process and account used to perform the uninstall.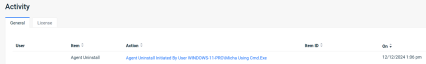
Select pages to include in the Executive Threat Report
To prepare for additional reporting enhancements, we have updated the Executive Threat Report. You can now select the pages to be included in the report from the library of available report pages. By having a library, we can continue to create new pages. You can select the pages to be included when creating a new report or editing an existing report.
Bug fixes
-
Some users have seen their Datto AV or Defender alerts listed as type DNS. This issue has been resolved.
-
When creating exclusions in a Windows Defender policy, the cursor would not move to a new line when pressing Enter. This has been resolved.
Artifacts
agent.macos-amd64.db3f40a939b72ff145a26801b96ed29df7df3003b091972d70263f1d0c20d757.bin.gz agent.macos-arm64.e3d385da3cac64384355dbc49e9d09035dc101b36c268caf74e376b67c778ede.bin.gz agent.linux-amd64.1d65baea07e84e925c5138d06e775019bfe344b03ebbbbc582c874138098ae1d.bin.gz agent.linux-arm64.e3d86b30543aa54f417b97e8299de54e28a5a121fd953511e68706c75b3589c7.bin.gz agent.linux-x86.90b4a3ec3a633abf8ae2ea0ab532397170836ecc2a265e3f44eac4ae674bd61e.bin.gz agent.windows-amd64.ba39b0e46aea9d719886f724473c2a586ed7b736b1c89195e61501fb4d0191de.exe.gz agent.windows-x86.1754a067df68d17814eec16e548226c9ee2ef6f2039a4e09457bf082163c46bb.exe.gz integrator.windows64.26ddd43e8fac5bd0308ea6d17b967e44b84aa393937170d8bbfd7d121585a757.exe.gz




