Understanding EDR and AV tamper protection
Tamper protection is a security feature designed to prevent unauthorized changes or disabling of critical system settings, files, or configurations. This article describes how to protect Datto EDR and Datto AV services from tampering, ensuring they remain active and secure against unauthorized interference.
Early Launch Anti-Malware (ELAM)
To understand the tamper protection provided by Datto EDR and Datto AV, it's important to first understand Early Launch Anti-Malware (ELAM).
Early Launch Anti-Malware (ELAM) is a Windows security feature introduced in Windows 8 and Windows Server 2012. It protects security software at the operating system's kernel (core process) level during boot, allowing trusted security solutions to start before third-party drivers and applications. This behavior extends the protected process infrastructure, which ensures that only trusted, signed code is allowed to load and defends against code injection attacks.
How ELAM Protects Processes
ELAM works by allowing certified anti-malware vendors to register their drivers as early launch drivers with Microsoft. These drivers load immediately after the Windows kernel (core processes) but before other boot-start drivers, enabling them to perform the following critical security functions early in the boot process:
- Evaluate and Block Boot Drivers: ELAM inspects and classifies drivers attempting to load during boot. If a driver is unknown or untrusted, ELAM can block it from loading.
- Establish Service Protection: Windows Code Integrity ensures that only trusted code is loaded into protected services. These protected processes run with enhanced privileges and are shielded from unauthorized code injection, even from processes running with administrative rights.
- Initialize Protection Early: By starting tamper protection and monitoring capabilities early, ELAM helps detect and stop threats before they can gain persistence.
Datto AV
Datto AV is an ELAM-certified solution. As part of the certification process, the drivers used in Datto AV were submitted to the Windows Hardware Quality Labs (WHQL) for rigorous testing, where they successfully demonstrated the critical security functions outlined earlier.
As a result, it is strongly recommended to implement Datto AV in your environment to enhance endpoint protection against service tampering.
Once deployed, Datto AV automatically protects its own processes and related files. Additionally, when installed alongside Datto EDR, it extends protection to the EDR service itself, preventing it from being terminated by unauthorized users or malicious actors.
Datto EDR
Most Endpoint Detection and Response (EDR) solutions are not traditional antivirus vendors and therefore cannot directly leverage ELAM certification.
Instead, EDR solutions typically:
- Layer on top of existing antivirus solutions which extends the tamper protection capabilities to the EDR process.
- Work within the constraints of user-mode and have limited access to the privileged layer of the operation system, which prevent tampering in certain scenarios.
As a result, there are inherent limitations in the tamper protection capabilities that EDR solutions can provide independently.
EDR tamper protection limitations
Unlike ELAM protected services, users with administrator rights on a system can perform the following actions:
- Disable services: An administrator can change the Service Startup type to Disabled, preventing the service from starting after the next system reboot. If not properly monitored, this can reduce the system’s security posture.
- Terminate processes: Non-ELAM protected processes can be terminated by an administrator. In such cases, a properly designed EDR agent should detect the termination and automatically restart the agent process to maintain protection.
EDR tamper protection recommendations
Enable tamper protection in your EDR policy
The Datto EDR policy includes a tamper protection option. When enabled, it prevents users from stopping or restarting the EDR service through the Windows Service Manager, which is the typical method used to stop services manually.
This setting can be configured on the EDR policy page by turning on Enable Tamper Protection.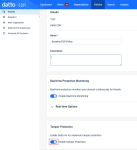
However, because EDR is a non-ELAM protected service, an administrator can disable EDR tamper protection if desired.
Administrative access controls
The tampering scenarios described require a user to have administrative permissions on the endpoint. By implementing controls that limit administrative access, organizations can significantly reduce the likelihood of such events occurring.
Examples of effective controls include:
- Role-Based Access Control (RBAC): Restrict administrative privileges to essential personnel only, ensuring users have the minimum level of access required for their roles.
- Just-in-Time (JIT) access: Grant temporary administrative privileges to users only when needed, reducing persistent admin rights and potential misuse.
- Granular permissions: Assign specific permissions instead of broad administrative rights, allowing for more controlled access to sensitive functions.
- Functional separation: Implement separation of duties across administrative roles to prevent any one user from having unrestricted control.
- Audit and monitoring: Continuously monitor administrative actions and access patterns to detect and respond to suspicious activity promptly.
Additional security measures
To further reduce risk, organizations should deploy additional security measures that can help detect or prevent unauthorized administrative actions. Examples include:
- Group Policy Enforcement: Use Windows Group Policy to restrict or prevent unauthorized modifications to services.
- Security Information and Event Management (SIEM): Implement a SIEM solution to monitor, alert, and respond to suspicious administrative activities.
- Network segmentation: Use network segmentation to limit the potential blast radius of a compromised administrative account, preventing lateral movement across critical systems.
Conclusion
While an EDR solution can offer some tamper protection functionality, it’s important to understand the differences between this and the protection provided by the Datto AV ELAM driver.
For maximum tamper protection, both Datto EDR and Datto AV should be deployed together, combining their capabilities to deliver a more resilient and secure endpoint defense.
| Revision | Date |
|---|---|
| Added ELAM & EDR tamper protection content. | 7/8/25 |