Understanding Datto EDR's Ransomware Detection
NAVIGATION Policies
PERMISSIONS Datto EDR subscription with administrator, analyst, or external analyst-level platform access
Datto EDR is a secure and fully-featured cloud platform that enables MSPs to remotely monitor, manage, and support their endpoints. It also provides an extra layer of security with native ransomware detection. Datto EDR's ransomware detection monitors for the existence of crypto-ransomware on endpoints by using proprietary behavioral analysis of files. Once ransomware is detected, Datto EDR can alert you, isolate the device, and attempt to stop the ransomware processes to keep the infection from spreading. When paired with Ransomware Rollback, ransomware detection offers a powerful early warning and rapid recovery system against malware.
This topic provides an overview of ransomware detection in Datto EDR and answers questions frequently asked by our partners. For details about Ransomware Rollback, refer to Working with Ransomware Rollback.
Key benefits
- Know about ransomware infections instantly. Instead of waiting for a user to report the issue, Datto EDR will notify you when files get encrypted by the ransomware. You'll have more time to respond and possibly prevent the spread.
- Easily monitor by using policy-driven configuration. The policy-driven approach of Datto EDR enables MSPs to monitor targeted devices easily and at scale for the presence of ransomware. Integrations with key MSP tools, such as Datto RMM, along with email and webhook notification options, ensure that the right resources can be immediately alerted if ransomware is detected.
- Prevent spreading of ransomware with automatic network isolation and termination of ransomware processes. Once ransomware is detected, you can have Datto EDR isolate the affected device from the network and attempt to stop suspected ransomware processes to prevent further spread of the infection to other devices.
- Remediate issues remotely. Devices automatically isolated from the network can still contact Datto EDR, enabling you to take effective action to resolve the issue.
- Recover with Datto Continuity products. When Datto EDR is integrated with Datto RMM + Datto BCDR, you can quickly recover from the ransomware outbreak by restoring the device to a previous state.
Requirements
- You must have an active Datto EDR subscription.
- Ransomware detection must be enabled and configured. For more information, refer to Ransomware configuration options.
- The Datto Endpoint Security agent must be installed on all endpoints you wish to monitor, and those devices must be able to communicate with your EDR instance.
IMPORTANT If you choose to run Ransomware Detection in Datto EDR, it must be disabled in Datto RMM or RocketCyber, and vice versa.
Compatibility
Ransomware Detection is supported on Windows 10 and above and Windows Server 2012 and above.
For more information, see Hardware and operating system requirements.
You'll find your ransomware detection settings on the Policies page. Clicking the name of a ransomware policy opens its Edit Policy page. From this location, the following configuration options are available.
Click any header to sort the displayed records by the column's value.
Ransomware monitoring options
| Details | |
|---|---|
| Field name | Definition |
|
Name |
The name of the policy |
| Description |
A brief description of the policy's purpose |
| Detection Options | |
|---|---|
| Field or feature name | Definition |
| Standard | Select to monitor any local drive for ransomware activity. Network drives, removable drives, and USB mass storage devices are excluded from being monitored. |
| Enhanced | Select to enable Datto Enhanced Ransomware Detection Monitoring. |
| Response Options | |
|---|---|
| Feature name | Definition |
| Kill Process |
When selected, Datto EDR will attempt to terminate malicious processes when they are detected, reducing the impact of a ransomware attack. |
| Isolate Host |
When selected, if ransomware is suspected on a host, the agent will automatically isolate the endpoint from all network connections except for the EDR portal. If this response is successful, Automatically shutdown infected systems will not execute. |
|
Shutdown |
When selected, in the event of a ransomware attack, EDR can automatically attempt to shut down infected systems. If Isolate Host or Kill Process are also enabled, EDR will attempt to complete those steps first. If Isolate Host is successful, the shut down response will not execute. |
File Recovery options
| File Recovery options | |
|---|---|
| Feature name | Definition |
| Disable | Select to prevent the deployment of the rollback agent and Rollback Driver Desktop application to endpoints monitored by your ransomware policy. |
| Full Disk Tracking |
Select to deploy the rollback agent and Rollback Driver Desktop application to all endpoints monitored by your ransomware policy. To learn how to leverage the recovery feature in your environment, refer to Working with Ransomware Rollback. When Full Disk Tracking is selected, the Include Additional Drives option appears. Select the check box to track changes with the Rollback Agent on any locWeal drive. Network drives, removable drives, and USB mass storage devices are excluded from monitoring. |
| Folders & Extensions |
Select to deploy the rollback agent and Rollback Driver Desktop application to all endpoints monitored by your ransomware policy. In this configuration, the rollback agent only tracks changes for user defined file extension types. When Folders & Extensions is selected:
|
| Preferences | |
|---|---|
| Feature name | Definition |
| Standard User Folders |
Select to track changes with the Rollback Agent on Standard User Folders which include (Desktop, Documents, Downloads) |
| Documents |
Select to track changes for the following file extensions (pdf, doc, docx, xls, xlsx, ppt, pptx, odt, ods, odp, txt, rtf, md, tex, csv) |
| Images | Select to track changes for the following file extensions (jpg, jpeg, png, gif, bmp, tif, tiff, svg, heic, heif) |
| Audio/Video | Select to track changes for the following file extensions (mp3, wav, aac, flac, mp4, avi, mkv, mov, wmv) |
| Archives | Select to track changes for the following file extensions (zip, rar, 7z, gz, tar, tar.gz, tgz) |
| Code Scripts | Select to track changes for the following file extensions (py, js, html, htm, css, json, xml, sh, bat, ps1) |
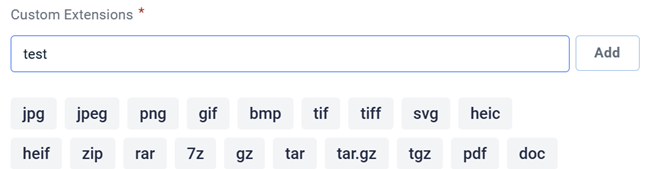
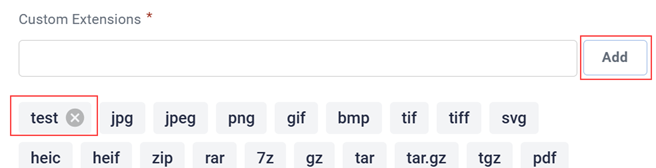
Custom Extensions
In the Custom Extensions section, you can specify additional file extension types that you would like the rollback agent to monitor.
Cache configuration options
Cache configuration is available only when Full Disk Tracking or Folders & Extensions are selected.
| Tracking cache size | |
|---|---|
| Feature name | Definition |
| Maximum Tracking History |
By default, the rollback agent will attempt to track changes for a seven-day rolling window. To reduce the retention period, select a value from this drop-down. |
|
Cache Size Type |
To track file changes and undo ransomware infections, the rollback agent creates a cache folder on each protected volume in which it stores historical file information. Once the cache space is exhausted, the agent will begin to purge file history. The value you specify here will be used for all monitored disks.
|
FAQs
Setting up ransomware detection is as easy as enabling it from the Policies page in your EDR portal. To get started, refer to Working with the Policies page.
Ransomware detection is designed to work alongside other security products you deploy to your customer endpoints.
Device isolation can be reverted by running the Host Isolation Restore extension from the Alerts page. Doing so will revert any isolation that has occurred on a device and return its ability to contact the internet and other devices on the network. Refer to Responding to alerts.
The Datto EDR ransomware detection engine looks for the existence of crypto-ransomware on endpoints by using proprietary behavioral analysis of files.
You can run a simulation package to test Datto EDR's ransomware detection. The simulation package (AutoRS.zip) and a set of instructions (Readme.txt) are available to download here.
NOTE How to get or run real ransomware is outside the scope of this procedure. The change described here is intended for demonstration purposes only and should never be left in place on an endpoint after the demonstration is complete.
EDR detects ransomware attacks by analyzing file update behavior and detecting file encryption. To test detection of ransomware, follow these steps:
- Configure EDR with ransomware detection enabled.
- Create a folder under the root (for example, C:\User\TestRWD).
IMPORTANT Do not create the folder in the Program Data, AppData, Temp directories or in any other folder not normally targeted by ransomware.
- Download the Ransomware Simulator (RanSim) from KnowBe4.
- Download the Datto RMM Ransomware Simulation Package (AutoRS2.zip).
- Copy the data folder from the simulation package to the folder created in step 2. The data folder contains normal-sized user files of several different types of files; for example, graphic files, text files, and so forth.
- Wait at least three minutes before starting the ransomware to avoid files being considered as transient.
- Download and start the ransomware. It can take up to a minute or more before the encryption process starts, depending on the type of ransomware.
- If the ransomware begins to encrypt files, EDR should create an alert and try to isolate the host.
If EDR does not create an alert, check the following:
- If the files in the user folder were not renamed or deleted, it is a sign that the ransomware did not start up or perform any encryption. This behavior can happen for many reasons; for example, the ransomware is outdated, the remote website the ransomware software attempts to connect to is no longer active, it has detected that it is running in a virtual machine, or it has detected that the keyboard of the machine is Russian or Ukrainian.
- If antivirus software is installed, it could block the ransomware. You should disable antivirus software and similar programs when testing.
- Simulation software, such as Ransim from KnowBe4, cannot be used directly because EDR detects that it is originating from a safe application. Use the modified version available from Datto instead. Refer to Can I test ransomware detection?
- If none of the above explained the missing alert, contact Kaseya Support.
We store the ransomware detection log on protected endpoints at %SYSTEMDRIVE%\ProgramData\Datto\Datto Rollback Driver\Logs\engine.log. Lines containing DETECTED indicate scans where ransomware detection identified a potential threat.
You can also view details about ransomware alerts from your EDR portal. For more information, refer to Working with the Alerts page.
| Revision | Date |
|---|---|
| How should I format exclusions? Edited answer. | 6/18/25 |
| Changed Supported operating systems to Compatibility: Edited - Ransomware Detection supports Windows 10 and above and Windows Server 2012 and above. | 11/18/25 |
| Global review, edits. | 12/17/25 |