Deploying the Datto Endpoint Security agent
NAVIGATION  > Organizations > select an organization > select a location >
> Organizations > select an organization > select a location > ![]() > Download Agent
> Download Agent
SECURITY Datto EDR subscription with administrator-level platform access or Datto AV subscription with administrator-level platform access
SECURITY Service account or administrator-level rights on the target endpoint
This article describes the process for directly installing the Endpoint Security agent on an endpoint. For alternate deployment methods, refer to the Additional resources section of this article.
NOTE Datto AV protection is delivered by the Datto Endpoint Security agent and is managed from the Policies page.
Prerequisites
Before you begin, we need to understand your current environment and what you'd like to do.
-
If you're a Datto EDR or Datto AV customer deploying the Endpoint Security agent to endpoints that currently don't have it, proceed to the next section of this article.
-
If you're a Datto EDR or Datto AV customer seeking to enable AV protection on one or more endpoints where the Endpoint Security agent is present, you do not need to redeploy any software. Refer to our Working with the Policies page article.
Direct installation
To monitor your endpoints, you'll need to install a lightweight software agent on all protected hosts.
IMPORTANT Verify that your endpoints meet the minimum hardware and operating system requirements. Refer to the article Hardware and operating system requirements
IMPORTANT This agent collects telemetry data and other information without dependencies on the underlying operating system. We have tested the Endpoint Security agent on the minimum versions of the platforms noted in this document and plan to support them indefinitely.
Download and install the Datto Endpoint Security agent by performing the following steps:
-
Log in to your EDR instance. In the top navigation menu, click Organizations.
-
Select the organization and the location to which you'll be deploying the agent. For more information, refer to Creating and managing organizations, locations, and devices.
-
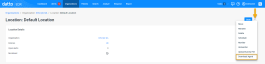
From the Location page, click the
 menu above the Location Details pane. Then, select Download Agent.
menu above the Location Details pane. Then, select Download Agent. -
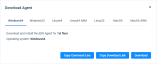
The Download Agent modal will open.
-
Select the installer that matches your endpoint's operating system.
-
To download the agent to your current computer, click Download.
-
To copy the installer's unique download link for use on another endpoint or to include in an installation script, click Copy Download Link.
IMPORTANT The download link is location-specific. You should not use it to deploy the agent to other locations in your organization.
-
-
Select a topic to continue.
Interactive install
-
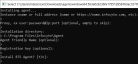
Run the installer as an administrator. A Command Prompt window will open.
-
Input the cname or full URL of your EDR instance (such as https://mycompanyname.infocyte.com). The URL will be supplied to you via email or by your EDR representative.
-
If the agent should use a proxy account, enter the username, password, IP address, and port information in the format shown by the installer.
-
Verify the installation directory. Make any necessary changes.
-
If you'd like to assign a human-friendly name for this agent, enter it when prompted.
-
Should you wish to automatically assign this agent to an organization and location, input a registration key. Doing so streamlines the process when you have hundreds or thousands of agents to manage at once. You can generate registration keys at
 > Admin > Agents > Registration Keys. For more information about managing organizations and locations, refer to Creating and managing organizations, locations, and devices.
> Admin > Agents > Registration Keys. For more information about managing organizations and locations, refer to Creating and managing organizations, locations, and devices. -
To begin the installation process, enter Y when prompted.
-
Once the installation completes, the Command Prompt window will automatically close.
Command line install
To install the agent via command line, run the executable within an administrator shell (such as PowerShell) in the following format:
SYNTAX: windows64.exe [FLAGS] [OPTIONS] [SUBCOMMAND]
EXAMPLE:
windows64.exe --key <Registration Key> --url https://mycompany.infocyte.com
FLAGS:
--debug Turn on debug logging
--enforce-https-certs Use TLS certificate validation (only use if providing own cert!)
--help Prints help information
--ignore-versioning Don't update local binary to match server
--no-extensions Don't run custom extensions
--no-install Do not install the agent, default = install
--no-intense-io Don't do any io-intensive file operations
--no-rts Do not run in RTS mode, only normal scans
--no-verify Don't verify the remote api is reachable
--quiet Do not send output to console (only log file)
--repl Launch lua repl with built in runtime extensions
--service Run as a service
--uninstall Remove HUNT Agent that was installed via --install
--version Prints version information
--verbose Turn on verbose logging
OPTIONS:
--url <api-url>
Sets the API URL (ex: https://192.168.1.1) to use for either generating a file or API communication
--auth <auth> Authenticator to use for auto-registration (optional)
--config <config> Use this as the configuration file
--database-name <database-name> Name of database to use for persistent storage
--extension <extension> Path to an extension or directory containing extensions
--friendly <friendly> Set a friendly name for this agent on the HUNT Server
--generate-config <generate> Create a new configuration file
--install-dir <install-dir> Specify directory in which to install HUNT Agent
--interval <interval> Sets the interval (in seconds) to use when pinging the API
--log-dir <log-dir> Sets the directory in which to store log files
--max-extension-run-time <max-extension-run-time> Max number of seconds an extension can run
--proxy <proxy>
Sets the optional HTTP proxy to use (ex: user:password@192.168.1.1:8080)
--key <server-key> Registration key (optional)
SUBCOMMANDS:
help - Prints this message or the help of the given subcommand(s)
survey - performs only survey actions, saving data to disk and exiting
Installation process
-
After you download the installer, open a Terminal session on your Linux system and run the following command to make the installer executable.
chmod +x linux64.exe
-
Next, launch the installer as a super user. Replace all values in brackets with the values corresponding to your instance.
sudo ./linux64.exe --key [Registration Key] --url [https://mycompany.infocyte.com]
-
Follow the prompts to install the agent.
Prerequisites
The Endpoint Security agent supports Apple endpoints with Intel x86 and Apple M1 (ARM) processors.
Download and Prepare
- Locate/create the location registration key:
- Select Admin.
- In the left navigation menu, click Registration Keys. If you do not see your location in the list, click the Add New Registration Key button. Save this key because you will need to add it in the agent installation command line.
- Download the agent:
- On the top navigation menu, click Organizations and click the applicable organization.
- Click the location on which you want to install the agent.
- In the upper-right corner, click the Download Agent button.
- Select the MacOS agent for your endpoint and click the Download button.
NOTE There are 2 chipsets: Mac Silicon and Mac Intel. It is important to know your build when downloading the agent. To find the chipset on the endpoint, click the Apple icon in the upper-left corner and select About this Mac.
Installation process
-
On your Mac, open Terminal from the Launchpad.
- Run the following command to navigate to the Downloads folder. To install the agent, you will be running commands from the Downloads folder. In the event you downloaded the agent to a different folder, make sure to run the following command with the applicable folder name.
cd ~/Downloads
- Run the following command to make the installer executable. This will ensure the EDR agent has the correct permissions to run as an executable. By using the chmod command you are telling the MacOS this file is safe to run, a necessary step in the installation process.
chmod +x ./agent.macos-amd64.<sha256 hash>.bin
- Launch the installer as a super user.
sudo ./agent.macos-amd64.<sha256 hash>.bin
NOTE If the same user who downloaded the file is logged into the system, sudo privileges are not needed since the user already has the necessary permissions.
- Follow the prompts to install the agent.
NOTE Rosetta is a compatibility layer that allows Intel-based apps to run on Apple Silicon (M1) processors. If prompted, allow the installation to proceed to ensure the agent runs correctly.
Alternatively, the agent can be installed with a single command line:
sudo ./agent.macos-amd64.<sha256 hash>.bin --url <instance URL>
NOTE The default installation directory is /usr/local/infocyte/agent. The service name will be HUNTAgent.
Wrapping up
If this agent deployment is for or will include Datto AV service, proceed to our Working with the Policies page article to continue.
Uninstallation
To remove the Endpoint Security agent from a Windows system, you can launch its built-in uninstaller via the Add/Remove Programs feature. Alternatively, you can run the following PowerShell commands on the endpoint.
PS > cd "C:\Program Files\Infocyte\Agent"PS > .\agent.exe --uninstall
To remove the Endpoint Security agent from a Linux or macOS system, you can either automatically or manually perform the uninstall from a Terminal session.
Automatic method
sudo /usr/local/infocyte/agent/agent.exe --uninstallManual method
systemctl stop HUNTAgent
systemctl disable HUNTAgent
rm /etc/systemd/system/HUNTAgent.service
systemctl daemon-reload
systemctl reset-failed
rm -rf /opt/infocyteAdditional resources
The following articles provide alternate methods to deploy the Endpoint Security agent: