Navigating the Respond page
NAVIGATION Respond
PERMISSIONS Datto EDR subscription with administrator or analyst-level platform access or Datto AV subscription with administrator or analyst-level platform access
BEFORE YOU BEGIN The type of subscription you have may define the features available to you on this page. For a comprehensive overview of features available to Datto EDR and Datto AV customers, refer to Datto EDR and Datto AV access control.
The Respond page enables you to view all pending and active responses to alerts in your environment. In addition, you can view and managed all files that the Endpoint Security agent identified and automatically quarantined while monitoring your endpoints.
This article describes the page's layout and functions. For information about responding to alerts in your environment, refer to Responding to alerts.
Overview
-
To access the Respond page, in the top navigation menu, click Respond.
-
If you're a Datto EDR subscriber only, when the page loads, you'll see the Responsesview, displaying a list of in progress and completed alert responses. If you're a Datto AV subscriber only, you'll see the Quarantined Files view.
Page features
The following tables define the features and information provided in each view available from the page's left navigation pane. Select a topic to learn more.
NOTE This feature is only available to Datto EDR subscribers.
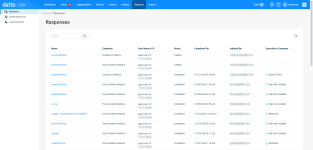
The Responses view enumerates all of the active and completed extension actions that users in your environment have deployed in response to surfaced alerts. From this location, you can view the process or object that triggered the response, the extension used, the endpoint to which it was deployed, and the outcome of the action. You can also export the information in the current view to a Comma-Separated Values (CSV) file.
Features
| Feature | Definition |
| Search |
Enter a partial or whole value to filter current view to matching records. |
|
|
Exports the information in the current view to a Comma-Separated Values (CSV) file |
Fields
NOTE Clicking any link in the table will open the alert, organization, location, or device detail page for the selected object.
| Column header | Definition |
|
Process Name |
Filename for most file-based objects, the hash of the memory content for memory injections, and the username for accounts |
| Extension |
The type of collection or response extension deployed by the user; review Leveraging collection and response extensions to learn more |
|
Host Name & IP |
The assigned hostname and IP address of the endpoint to which the extension was deployed |
|
Status |
Indicates the current progress of the extension's execution |
|
Completed On |
Date and time at which the extension's execution finished running on the endpoint |
|
Initiated By |
Username of the individual initiating the alert response |
|
Execution & Summary |
The outcome of the extension's execution and details about any actions taken |
NOTE This feature is only available to Datto EDR subscribers.
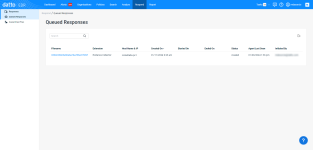
The Queued Responses view lists all of the extension actions that users in your environment have deployed in response to surfaced alerts but which have not yet initiated. From this location, you can view the process or object that triggered the response, the extension used, the endpoint to which it was deployed, and the status of the action. You can also export the information in the current view to a Comma-Separated Values (CSV) file.
Features
| Feature | Definition |
| Search |
Enter a partial or whole value to filter current view to matching records. |
|
|
Exports the information in the current view to a Comma-Separated Values (CSV) file |
Fields
NOTE Clicking any link in the table will open the alert, organization, location, or device detail page for the selected object.
| Column header | Definition |
| Filename |
Filename for most file-based objects, the hash of the memory content for memory injections, and the username for accounts |
|
Extension |
The type of collection or response extension deployed by the user; review Leveraging collection and response extensions to learn more |
|
Host Name & IP |
The assigned hostname and IP address of the endpoint to which the extension was deployed |
|
Created On |
Date and time at which the extension's execution was queued |
|
Started On |
Date and time at which the extension's execution began to run on the endpoint |
|
Ended On |
Date and time at which the extension's execution finished running on the endpoint |
|
Status |
Indicates the current progress of the extension's execution |
| Agent Last Seen | Last date and time that the EDR platform received telemetry from the host. |
|
Initiated By |
Username of the individual initiating the alert response |
NOTE This feature is only available to Datto AV subscribers.
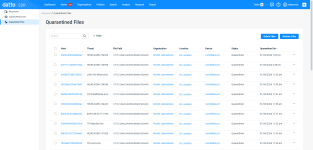
The Quarantined Files enumerates all files that the Endpoint Security agent identified as potentially malicious and automatically quarantined. From this location, you can review the details of the suspected threat objects, along with their corresponding alerts, and take actions to delete or restore the content. As you navigate, you'll see the following features and fields:
Features
| Feature | Definition |
| Search |
Enter a partial or whole value to filter current view to matching records. |
| Filter |
Includes or excludes results in the report based on Host, Organization, and Location. Status values, and on From and To dates. Numeric value appearing next to this button indicates number of filters currently applied |
| Delete Files |
Permanently deletes the selected file(s) |
| Restore Files |
Restores the selected file(s) |
IMPORTANT If some features, like restore files, are not available, verify that the Real-time Protection Scan feature OR the Alert-Only Action on Detection feature is enabled for your Datto Antivirus policy. Both features should not be enabled at the same time.
Fields
NOTE Clicking any link in the table will open the alert, organization, location, or device detail page for the selected object.
| Column header | Definition |
|
Alert |
The unique ID of the alert associated with the quarantine action |
|
Threat |
The specific cataloged threat or vulnerability that the object appears to match |
|
File Path |
Full path on the impacted endpoint where the suspicious object was found |
|
Organization |
Name of the organization associated with the object |
| Location | Identity of the location associated with the object |
|
Device |
The hostname of the device on which the suspicious object was found |
|
Status |
Indicates the current status (Quarantined, Restored, Deleted) of the object |
| Quarantined On | The time and date at which the analysis engine observed the object |
| Actions menu; enables you to delete or restore the object |