Leveraging collection and response extensions
NAVIGATION Alerts > ![]() > Respond
> Respond
PERMISSIONS To upload and enable extensions: Datto EDR subscription with administrator-level platform access
PERMISSIONS To deploy response extensions: Datto EDR subscription with analyst-level platform access
In addition to the plethora of native host data collection and analysis included with Datto EDR by default, you can define your own collection and response actions to be performed on endpoints in your environment.
This article describes the extension system and how to start using it.
Overview
Our extension system is built on top of Lua 5.3, providing an easy-to-deploy, cross-platform, and feature-rich library of built-in functions. These functions include file system, string, I/O, and math operations. In addition, we make the capabilities of our agent and endpoint collector available to you so that you can build powerful and convenient extensions capable of performing actions such as:
-
making web requests.
-
accessing the Windows registry.
-
terminating running processes.
-
adding items to the result set retrieved by the platform's standard host collection routine.
-
calling PowerShell, Python, and Bash scripts.
We currently support two types of extensions: collection and response. The extensions included with Datto EDR are active by default.
Collection extensions extend the data collected or inspected by Datto EDR at scan time. Such data can include additional registry keys and files to be analyzed or YARA signatures to be used on the host side.
You can also create custom logic capable of flagging threat statuses or collecting text fields up to 3 MB in size. For data collection beyond this threshold, collection extensions support the export of data directly from the endpoint to your Amazon S3 Bucket, sFTP, or SMB share.
Response extensions can perform direct actions on and change the configurations of remote systems. For example, you can build extensions that take remediation actions such as host isolation, malware removal, and killing running processes. You can also build proactive response actions that harden hosts or install third-party tools.
The following pre-built extensions are included in your Datto EDR platform.
| Extension name | Description |
| AV Check |
Integrates with Windows Security to retrieve and validate configurations |
| Artifact Scanner |
Uses Zimmerman's Amcache parser to review the Amcache hive and add those entries to artifacts for analysis; supplements basic artifact scan conducted by the agent but is more resource-intensive |
| Delete File |
Deletes a file by path; for more information, refer to Deploying the delete_file extension |
| Evidence Collector |
Collects raw event logs, .dat files, history, etc., from an endpoint, packages them, and forwards them to your provided recovery point
|
| Filesystem Scanner |
Scans the system for filenames matching a set of RegEx patterns, such as ransomware notes |
| Force System Reboot |
Forces system reboot after delay |
| Host Isolation |
Performs a local network isolation of a Windows or Linux system by using a filter driver on Windows and iptables or ipfw on Linux |
| Host Isolation Restore |
Reverses the local network isolation |
| RDP Log Scanner |
Uses RDP lateral movement to gather and combine logon events (4624, 4778, 4648), with RDP session events (21, 24, 25, and 1149) with processes started (4688) by those sessions |
| Run Command |
Runs a command on the target host (Bash, PowerShell, or CMD) IMPORTANT Use with caution. |
| Terminate Process |
Kills a process by path or deletes the associated file |
| Yara Scanner |
Scans files on disk with YARA signatures categorized as either informational, suspicious, or bad |
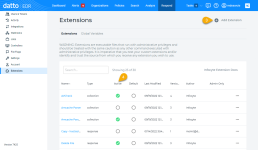
Before you can use extensions, you must enable them. To do so, perform the following steps:
-
The Extensions page will load.
-
To create a new deployable solution, click Add Extension, complete all applicable fields, and then click Save. The new executable file will appear in the list of available solutions.
-
To enable an extension, check its corresponding selector in the Active field. If the selected executable file is a response action, it will become available at Alerts >
 > Respond.
> Respond. -
To disable an extension, clear its selector.
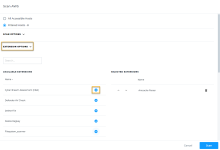
You can configure any enabled extension to run at each scan interval. To do so, perform the following steps:
-
In the top navigation bar, click Organizations.
-
Select a location.
-
Click Scan. The scan configuration options for the selected location will open.
-
Click Extension Options. To designate extensions that should run during each scan, click the
 icon next to its name. The deployable solution you've selected will move into the Selected Extensions column. To remove an extension from the scan, click the corresponding
icon next to its name. The deployable solution you've selected will move into the Selected Extensions column. To remove an extension from the scan, click the corresponding  icon.
icon.
When you're ready to start building your own extensions, consult our Datto EDR extension docs (GitHub), where you'll find code examples and downloadable extensions contributed by your fellow users.