Getting Started with Datto EDR and Datto AV
This article provides the recommended steps to begin the Datto EDR onboarding process. You should perform the process in the order it is presented.
Accessing Datto EDR the first time
The first time you log in to Datto EDR, you will access the application through the Datto Partner Portal (auth.datto.com/login).
- Kaseya 365: If you are using Datto EDR as part of your Kaseya 365 subscription, your experience starts in KaseyaOne. Follow the instructions in the Kaseya Welcome email you received. In KaseyaOne, when you click the Activate link for your new Datto EDR module, you will be redirected to the Datto EDR Set Your Password modal. Follow the steps below to set your password and enable two-factor authentication.
- Standalone Datto EDR: If you are a standalone customer for Datto EDR (you don’t have a Kaseya 365 subscription) and you don't have any modules accessed through Datto Partner Portal, you will access Datto Partner Portal through your Welcome to Datto Partner Portal email.
The log in steps are outlined in the following steps:
- Access Partner Portal through your Activate link (365 customers) or your welcome email (standalone customers).
- In the Set Your Password pop-up window, type a new password and click Set Password.
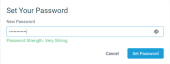
- On the next page, click Log In.
- Log in with your credentials, using your new password.

- In the Select Authentication Method modal, follow the steps to set up two-factor authentication.
- If you only have Datto EDR module access, you will be logged in directly to Datto EDR.
If you have more than one Partner Portal module (any Datto backup product, Datto EDR/AV, SaaS Protection, Datto RMM) currently, you will see the account selection page.
Click the Continue button for the Datto EDR module.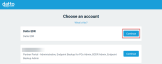
Onboarding
This Onboarding section guides you through the essential planning tasks required to ensure a successful onboarding experience.
IMPORTANT Go through each Onboarding section before implementing EDR. This will help ensure that when you do implement EDR, you successfully protect your organization's endpoints from malicious activity without causing network issues.
Setting up accounts
We recommend adding one or two admin user accounts as backup accounts. These accounts are created within auth.datto.com that the user can use along with their Kaseya 365 login.
You can add new accounts by hovering over your username in the top-right corner and selecting Admin.
Then on the Users & Tokens page, you would click the Add User button.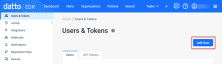
Configure KaseyaOne Unified Login
If you are a Kaseya 365 customer, return to your Kaseya 365 Setup Guide to configure KaseyaOne Unified Login. After you complete this step, you will return to Datto EDR to complete the self-guided onboarding that launches automatically the first time you log in and will continue to prompt you to complete until you finish all your onboarding tasks.
If you are a standalone Datto EDR customer, it is also recommended that you configure KaseyaOne Unified Login for easy access to all your IT Complete modules. Refer to the article Integrating with KaseyaOne.
Reviewing default policies
EDR activates a few essential policies by default. These default policies will help you learn about your network security behaviors without disrupting network operation. The active default policies are accessible on the Policies page and are described below:
- EDR real time monitor: EDR real time monitor is an active default Datto EDR policy that performs real-time analysis and performs behavior detections.
The preferred EDR deployment mode is to enable real-time monitoring, not enable scheduled scans. - Datto AV Alert only: Datto AV Alert only is intended to scan files only. It does not quarantine files. It is a recommended policy for deploying new agents so you can learn what needs to be allowlisted.
Real-time protection scans should be run on a scheduled basis during low usage times and set to perform full scans, not for selected files. -
Ransomware Protection: Ransomware Protection will monitor for any ransomware behavior and in the event of detection, it will attempt to isolate the host and kill the suspected process.
The Rollback and File Recovery feature is only available when the Ransomware Detection policy enabled in EDR. It is not available when ransomware detection is enabled in Rocketcyber or RMM.
Planning your organization structure
EDR provides various options for adding organizations. On the Organizations page, you can click the Add Organization button to add an organization and then add locations.
If you integrate EDR with RMM or VSA, the organizations and locations in these platforms automatically synchronize to EDR.
To integrate with RMM, you will need to create an API token on the Admin > Users & Tokens page.
You will need to enter the API token in the RMM platform to complete the integration.
You can integrate with VSA simply by clicking Integrations in the navigation menu and clicking the VSA tile.
Deploying the EDR agent
An EDR agent must be deployed to each endpoint you want monitored and protected.
You can deploy EDR automatically through your integrations with RMM or VSA , or you can manually install the agent.
After selecting the organization, you’ll navigate to the All Locations page and click the desired location.
The Download Agent button will display the modal where you select the applicable operating system.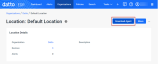
Clicking the Copy Command Line button will install the agent to all of the selected location’s devices.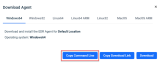
Monitoring alerts and quarantined files
After deploying the EDR agents, you will be able to monitor alerts and quarantined files.
The Alerts page contains a list of suspected threats detected by the Datto EDR or Datto AV.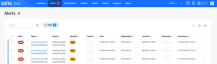
Any files that are automatically quarantined by Datto AV can be reviewed and managed by selecting Respond > Quarantined files.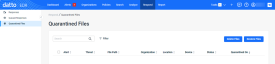
IT Complete integrations
Depending on the other IT Complete modules active in your stack, you can take advantage of the following integrations to improve security and overall operations:
- RMM: Understanding the Datto EDR + Datto RMM integration
- Autotask: Configuring the Autotask integration
- BMS:Configuring the BMS & Vorex integration
- RocketCyber: Configuring the RocketCyber - EDR integration
- VSA 10:Configuring the VSA 10 integration



