Inspecting AWS EC2 Instances with Datto EDR Cloud
ALERT LEGACY ARTICLE: The content in this article is no longer updated and is available for reference purposes only. Features and workflows described may be deprecated, significantly changed, or no longer supported.
Environment
- Datto EDR
Description
The Datto EDR Cloud Workload Security module is very simple to configure and does not require deploying code, agents, virtual appliances, or containers into the target network. However, some conditions must be in place to allow for proper analysis of these assets.These conditions are:
- AWS Systems Manager (SSM) Agent must be running on target EC2 Instances.
- AWS IAM Account access key with an AWS SSM Policy applied to allow SSM actions.
- Creation of a new Query and Credential within Datto EDR HUNT Console.
- This is an AWS Query only and will not contain targeted AWS IP ranges.
- This Query will use the AWS IAM Role Access Key and Secret Pair.
To begin leveraging this new capability, you must complete the following actions:
- Have AWS Systems Manager (SSM) enabled on target hosts. Â AWS SSM Agent is installed and available by default on the following AMIs:
- Windows Server (all SKUs)
- Amazon Linux
- Amazon Linux 2
- Ubuntu Server 16.04
- Ubuntu Server 18.04
More information can be found at https://docs.aws.amazon.com/systems-manager/latest/userguide/ssm-agent.html
- Create an IAM Role (programmatic access only is needed) or use an existing IAM Role with access key and secret pair, with an AWS SSM policy defined, that allows key SSM capabilities for the resources. This policy must include the following Allow Actions:
- i. ssm: CancelCommand
- ii. ssm: SendCommand
- iii. ssm: GetConnectionStatus
- iv. ec2: DescribeInstances
- v. ssm: DescribeInstancesInformation
See the following example policy:
"Statement": [
  {
      "Sid": "ExamplePolicy",
      "Effect": "Allow",
      "Action": [
      "ssm:CancelCommand",
      "ssm:SendCommand",
      "ssm:GetConnectionStatus",
      "ec2:DescribeInstances",
      "ssm:DescribeInstanceInformation"
      ],
      "Resource": "*"
  }
   ]
}
3. In the Datto EDR Cloud console create a new Target Group, or edit an existing Target Group.
4. Add a New Query, clicking the Add Query Icon.
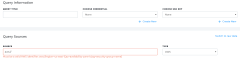
5. Provide a friendly name under the Query Title field.
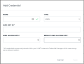
6. Add a new credential, by clicking the Create New icon under the Choose Credential field in figure 1.
7. Change the Source Type to AWS, and Enter the AWS Path in the source field.
8. Save the new query, and enumerate the recently created query by clicking on the find hosts icon in the Target Group Window.
9. Once the enumeration task is completed, click the Scan icon to initiate the first analysis of the assets in this target group.