Datto EDR: Agentless scanning Credential Quick Start
ALERT LEGACY ARTICLE: The content in this article is no longer updated and is available for reference purposes only. Features and workflows described may be deprecated, significantly changed, or no longer supported.
Topic
Agentless scanning Credential Quick Start
Environment
- Datto EDR
Description
Credential Manager
Agentless collection uses credentials that you define in Datto EDR's Credential Manager. This requires a service account or administrative credential with Administrator-level rights on each of the target endpoints.
-
SSH Credentials can be Key-based or Username/Password or both.
-
The SSH account must be part of the sudo group and should not be the root account.
-
These are encrypted using a server-side key by default but can also utilize a client-side encryption (AES Key) generated by the Controller to further protect the credentials.
-
To add credentials for use with Agentless Scanning an end-user with administrative privileges will navigate to the Credential Manager under the Administration console.
Adding Credentials
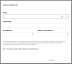
In the administration console navigate to the Credential Manager and select the Add Credential button on the Credentials tab. The Admin will be presented with the following fields.
-
Name: Friendly Name
-
Username:Domain\Username or .\username for non-domain joined machines.
-
Password: Enter a complex password.If AES Encryption is to be used, this will be the only time the password will be entered.
-
Encrypt client-side using my passphrase: Select this box if AES Encryption is to be used and enter the passphrase in the two additional fields.
Select Save to complete the changes.
Adding SSH keys for Linux
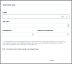
In the administration console, navigate to the Credential Manager and select the Add SSH Key button on the SSH Keys tab. The Admin will be presented with the following fields.
-
Name: Friendly Name
-
SSH Key: Enter the SSH Key
-
Password: Enter a complex password. If AES Encryption is to be used, this will be the only time the SSH key will be entered.
-
Encrypt client-side using my passphrase: Select this box if AES Encryption is to be used and enter the passphrase in the two additional fields.
Additional SSH Key Information
Datto EDR HUNT allows for SSH authentication using key pairs, within our tool for authenticating endpoints within your network. As the HUNT controller can scan Linux endpoints running OpenSUSE, Debian, Ubuntu, Red Hat, CentOS, and Fedora, Datto EDR can also use SSH keys to authenticate to the endpoint. To do this, you must first complete the action below:
Prepare and gather SSH keys on your endpoints. If you have multiple Linux endpoints and want to authenticate using SSH on all of them, you will need the public key of each Linux machine. If you are not sure how to generate an SSH key on your machine, please https://www.ssh.com/ssh/keygen/ to learn how to generate an SSH key. Once that is generated, you will need to copy the public key to the .ssh folder on the Linux system. The file with the public key will end in .pub, which is the extension for the file with the public key. You should add a passphrase to the private key, which is something you will need to make note of as Datto EDR HUNT will need that information in order to authenticate against the remote endpoint.
Running the Scan or Schedule in "Temporary" Mode
To then run the scan as an "Agentless" (i.e. a Temporary agent will be deployed) on Target Group page select Find Hosts and Scan with the Agent Persistence Options set to Temporary. See the following for Creating target groups and adding agents.