Agent vs Agentless
ALERT LEGACY ARTICLE: The content in this article is no longer updated and is available for reference purposes only. Features and workflows described may be deprecated, significantly changed, or no longer supported.
Environment
- Datto EDR
Description
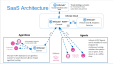
Datto EDR Cloud supports both agent-based and agentless endpoint access models that can be used in parallel or separately.
Agentless:
Agentless endpoint access is achieved through the use of native remote management protocols like WMI, SMB, Remote Scheduled Tasks, and PSRemoting for Windows-based systems and SSH for Linux-based systems. This methodology is appropriate for centrally managed networks where you don't want to install permanent agents or don't want to make permanent changes to the systems (this bypasses most organization's more stringent Change Control processes since it isn't producing a change to the baseline of the system).
Credentials used for agentless collection will utilize credentials defined in Datto EDR's Credential Manager. This requires a service account or administrative credential with Administrator-level rights on each of the target endpoints. SSH Credentials can be Key-based or Username/Password or both. The SSH account must be part of the sudo group (should not be root account). These are encrypted using a server-side key by default but can also utilize a client-side AES key generated by the Controller to further protect the credentials.
In un-monitored mode, collection is performed by the Survey module (survey.exe) which is pushed and remotely executed on each system by a Controller. This Survey is temporary and will only last for the duration of the scan after which it will self-delete (typical duration = 3 minutes, timeout defaults to 60 minutes). On 64-bit Windows systems, a 64-bit s1.exe will be dropped from survey.exe once the architecture check is complete. Once complete, the survey will automatically return the results to the SaaS instance it is paired with. If it cannot, it will drop the results to the default temp folder and can be manually collected for offline/manual scan processing.
In monitored mode, Real-Time Security is achieved by pushing an agent to the remote system by a Controller. This agent resides on the machine until it is removed from the monitored target group. Real-Time information is sent around process launches every 15 minutes, and a full deep-scan occurs once a day in this mode.
Devices can be part of both a Monitored target group and an un-monitored target group, but can not reside in two monitored target groups at once.
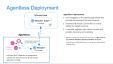
The Controller is the component that facilitates agentless and monitored endpoint access inside the firewall of the target network. This system must have access on the supported protocols to target endpoints. Nothing is processed or stored on the Controller, it merely acts as a relay for scanning.
Asset Discovery must be performed by defining Queries which can be a CIDR block, IP Address Ranges, specific hosts, or AD/LDAP domains.
Agent:
Agents can also be installed permanently or semi-permanently on endpoints. This provides the Datto EDR instance with direct access for collection without the need for credentials or remote admin protocols. This is appropriate for mobile devices that jump from network to network or for networks that do not use centralized management protocols that Datto EDR HUNT supports.
Agents simply need to connect to the HUNT instance on HTTPS (TCP 443).
Registration Keys can be used to automatically approve and add newly installed agents to a paired Target Group. Agents can be added to multiple target groups as well.
Agents in monitored, or unmonitored Target Groups behave the same way as outlined above for the Agentless based access method.
Hybrid:
If both agents and a Controller is deployed into a network. The Agent will be favored for a particular IP address. If the agent is not running, accessible agentless methods will be used as a secondary method.