What are EDR detection rules?
NAVIGATION Policies > Detection Rules
PERMISSIONS Datto EDR subscription with administrator-level platform access or Datto AV subscription with administrator-level platform access. Service account or administrator-level rights on the target endpoint.
IMPORTANT Infocyte-created rule bodies can only be copied, modified or viewed by our internal detection engineers. Users can create and edit their own custom rules if desired.
NOTE Alerts generated by the rules engine display the rule body on the Alert Detail page. For more information, see the article Understanding the Alert Detail page.
This article defines EDR detection rules and explains how to build and edit your own rules using the "Detection rules style guide."
Detection rules background
Detection rules run automatically against endpoint audit data as it is received by your instance. These rules help Datto EDR identify potential threats and determine how to address them. The rules we provide analyze your endpoints for processes and behaviors that align with the most common Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) techniques. When a rule is triggered, Datto EDR generates an alert and follows the workflow you have defined in your Automated Response Policy.
You can selectively enable, disable, and customize rules to tailor your instance's threat analysis procedures to the specific needs of your environment. These management options are available on the Detection page.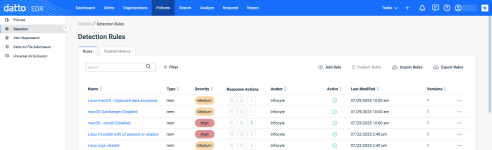
When you visit the Detection Rules page, the Rules view is selected by default.
| Feature | Definition |
| Rules |
Click to switch to the Rules view |
| Publish History |
Click to view a log of rule publication activity for your instance |
| Search |
Enter a partial or whole value to filter current view to matching records.; click Filter to apply additional search criteria |
| Add Rule |
Enables you to create a new detection rule by using the rule editor; for more information, refer to the Adding or editing rules section of this article |
| Publish Rules | Click to publish new rules and rules with configuration changes since the last publish |
| Import Rules |
Enables you to import new rules in YAML format; maximum file size is 100 MB. |
| Export Rules |
Enables you to export existing rules in YAML format; only custom rules can be exported |
| Field name | Definition |
|
Process Name |
The name of the rule; clicking it will open the rule editor; for more information, refer to the Adding or editing rules section of this article |
|
Defines the characteristics that must be met before Datto EDR will act on the rule: Item: Agent will evaluate, alert, and take action against individual events as they are received to determine if the events are notable attacker behaviors EXAMPLE A PowerShell command's arguments would be evaluated by the rule and identified as a Correlation: Agent will evaluate all recent behaviors observed to determine if there is a pattern of threat behavior and, if so, act accordingly EXAMPLE A |
|
|
Severity |
The severity level of the alert that will generate if the rule is triggered |
| Response Actions |
If the rule is capable of automated response, indicates the type of action the Endpoint Security agent will attempt to take upon detection of a threat; the following values are possible:
|
| Author |
The name of the author who created the rule |
| Active |
Click the icon in this field to activate or deactivate the policy; |
| Last Modified |
The time and date the rule was last updated |
| Versions |
Indicates how many versions of this specific rule have existed in your instance; version number iterates each time the rule is modified |
|
|
Click to delete the rule or view its previous versions |
The Publish History view displays a log of rule publication activity for your instance.
| Feature | Definition |
| Rules |
Click to switch to the Rules view |
| Publish History |
Click to view a log of rule publication activity for your instance |
| Search |
Enter a partial or whole value to filter current view to matching records. |
| Field name | Definition |
| Published On |
The date and time of the rule's publication |
| Published By |
The identity of the user or process that published the rule |
From the Detection Rules page, click Add Rule or click the name of an existing rule to open the editor. Populate or change the following fields, and then click Save.
IMPORTANT Once you create or edit an existing rule, you'll need to ensure that it's active and then click Publish Rules on the Detection Rules page before it will go into effect.
| Field or feature name | Definition |
|
Process Name |
The name of the rule |
| Actions |
When active, rule will generate alerts; when inactive, no alerts will generate |
|
Severity |
The severity level of the alert that will generate if the rule is triggered |
| MITRE ID |
The specific MITRE ATT&CK knowledge base ID to which the rule maps |
| MITRE tactic |
The specific MITRE ATT&CK tactic to which the rule maps |
| Short description |
A brief description of the rule that will appear in alerts that it generates |
| Rule type |
Defines the characteristics that must be met before Datto EDR will act on the rule: Item: Agent will evaluate, alert, and take action against individual events as they are received to determine if the events are notable attacker behaviors EXAMPLE A PowerShell command's arguments would be evaluated by the rule and identified as a Correlation: Agent will evaluate all recent behaviors observed to determine if there is a pattern of threat behavior and, if so, act accordingly EXAMPLE A |
| Description | The extended description of the policy's purpose, functions, and any other pertinent information |
| Rule Body |
Free-text editor in which you can specify the endpoint actions that Datto EDR should take if this rule is triggered; all syntax must be in YAML format |
Detection rules style guide
The Infocyte Query Language (IQL) is a custom language used to build detection rules. It is powerful yet familiar, and simple enough for non-programmers to learn quickly.
The Infocyte Query Language (IQL) is loosely based on JavaScript and related programming languages. It is designed to be familiar, easy to learn, and intuitive to use.
No need to escape (normally)
IQL is designed to simplify interaction. For example, copy-pasting Windows file paths is straightforward. Strings are handled naturally without requiring escape characters.
If you need advanced string handling, we recommend using the regex() function.
Usage
Detection rules contain two parts:
- A conditional statement – written in IQL, similar to JavaScript.
- Supports boolean operators (&&, ||)
- Allows grouping and exclusions
- Includes useful functions for working with endpoint data types
- An action – executed when the condition evaluates as true.
For more details on IQL syntax, see the API Reference section below.
API Reference
Rules are evaluated against data collected by the EDR agent on the endpoint.
- All data types contain a
typefield. -
Any collection involving files on disk includes properties such as:
- path
- md5
- sha1
- sha256
Detection rules in the Infocyte Query Language (IQL) can range from simple equality checks to complex expressions using functions, operators, and regex.
Basics
Simple rules
You can create simple rules using equality (==) or inequality (!=) operators:
path == "c:\users\john\malware.exe"Advanced rules
Complex rules can combine multiple conditions with boolean operators (&&, ||) and grouping:
path == "c:\users\john\malware.exe" || (path == "c:\users\*\ignore-me.exe" && parentPath != "c:\windows\system32\explorer.exe")
Functions
Several functions are available to help simplify working with data.
Here is example input used to demonstrate each function.
{"path": "c:\\windows\\system32\\notepad.exe",
"commandLine": "c:\\windows\\system32\\notepad.exe c:\\users\\joe\\Documents\\Passwords.TXT",
}
lowercase()
Transforms a string or field to lowercase.
Examples of valid rules to make EDR alert to items that have a path equal to c:\windows\system32\notepad.exe
path == lowercase("C:\windows\System32\NotePad.EXE")lowercase(commandLine) == "c:\windows\system32\notepad.exe c:\users\joe\documents\passwords.txt",
lowercase("StRIng") == lowercase("stRing")
uppercase()
Transform a string or field to its uppercase. Functions the same way as lowercase().
regex()
Provides PCRE-compliant regex matching framework.
path == regex(".*notepad\.exe")
iregex()
Convenience wrapper for case insensitive PCRE compliant regex matching.
commandLine == iregex("\.txt")
Which is equivalent to:
commandLine == regex("(?i)\.txt")
date()
Supports parsing and comparing dates in multiple formats:
-
yyyy-mm-dd
-
yyyy-mm-dd HH:MM
-
yyyy-mm-dd HH:MM:SS
-
yyyy-mm-ddTHH:MM:SSZ (ISO format)
date('2020-01-01') < date('2021-01-01')
This operation works on fields as well:
date(createdOn) > date('2021-01-01')
today()
Returns the current date/time for comparisons.
date(createdOn) > today()
trailingDays()
Returns the date/time for the number of days prior to today.
The following matches any created date within the last 30 days:
date(createdOn) > trailingDays(30)
cidr()
Generates a network CIDR for matching IP.
type == "connection" && remote_addr != cidr("192.168.1.0/24")
privateIp()
Matches IPs against private or loopback ranges.
The following matches all destIp instances that are not loopback or private:
type == "connection" && remote_addr != privateIp()
IMPORTANT It is highly recommended that you deploy new detection rules in Non-Alert mode for initial testing. This prevents excessive alerts or unintended automated responses.
Detecting a process with a specific hash
General Rule
type == "process" && (*type can also be modules, drivers, autostarts, artifacts)
name == "Name.exe" &&
sha1 == "sha1_hash" (*can also be sha256 hash)
Specific Example: Calculator.exe
type == "process" &&
name == "Calculator.exe" &&
sha1 == "80865A5563EB92B8653A5AF3DB371D7BC1674B2D"
Detecting a network connection from a process with a specific hash.
General Rule
item_type == “connection” &&
process_sha1 == "sha1_hash" (*can also be sha256 hash)
additional conditions can be added to this General rule like local/remote address (localaddr, remoteaddr) or local/remote port (localport, remoteport)
Specific Example: Calculator.exe
Alerting on network connections initiated by Calculator (calc.exe)
item_type == “connection” &&
process_sha1 == "80865A5563EB92B8653A5AF3DB371D7BC1674B2D"
Detecting process execution in non-standard directories.
NOTE In some regex rules, the backtick (``) is used as a quote character. This allows both single (‘ ’) and double (“ ”) quotes to be used inside the regex string without being interpreted as string terminators.
type == “process” && path ==iregex (`\\AppData\\Local\\Temp\\` || `\\Downloads\\` || `\\AppData\\Roaming\\`)
Detecting suspicious command-line activity. Alert to users running findstr.exe looking for passwords.
type == "process" &&
lowercase(name) == "findstr.exe" &&
commandLine == iregex("password")
| Revision | Date |
|---|---|
| Initial release. | 9/8/25 |